Adversarial SecOps
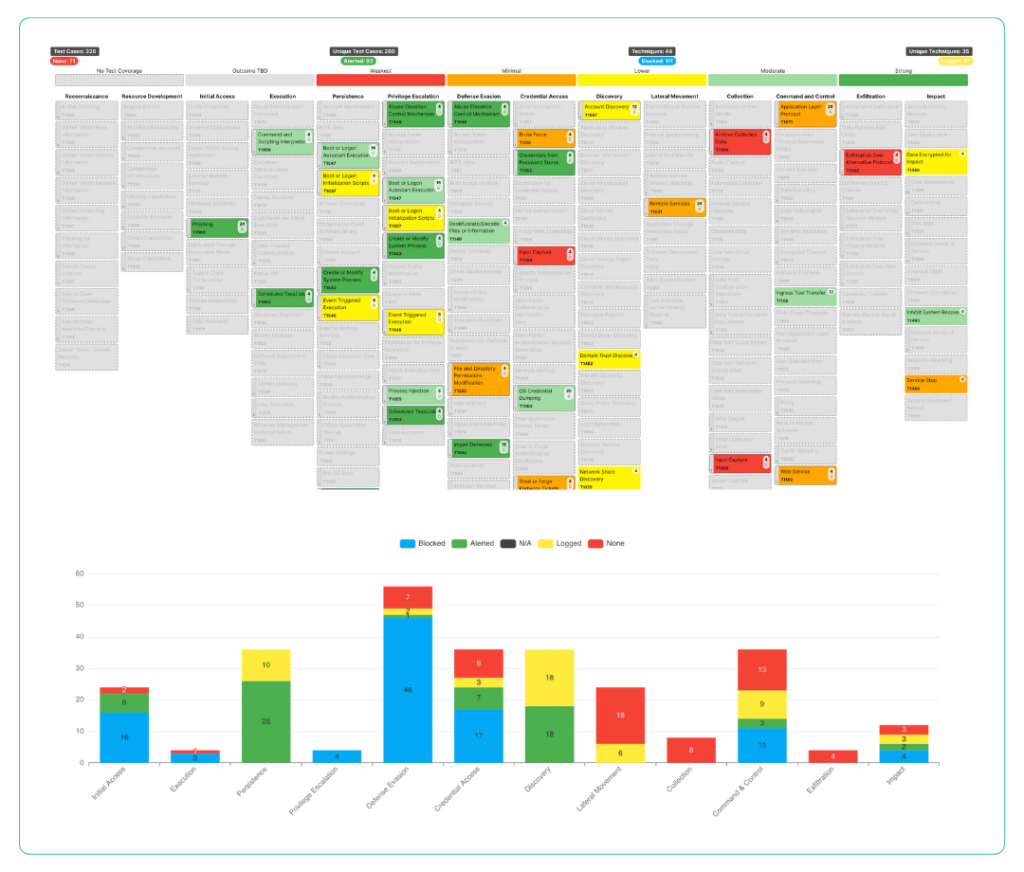
Data Exfiltrate and Active Directory Assault
Threat actors end goal usually is to exfiltrate your corporate data, compromise your domain controller before deploying ransomware.
We conduct a thorough Data Exfiltration and Active Directory Assault and execute threat actor techniques such as credential dumping, lateral movement, data exfiltration, persistence through command and control.
Our goal is to ensure every technique used is detected and blocked.
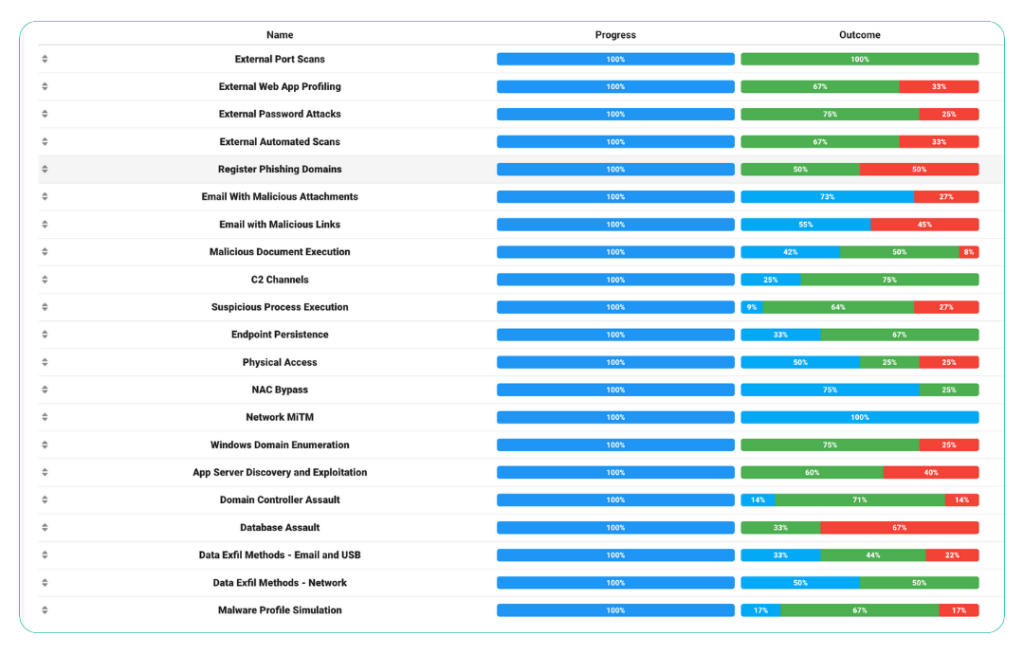
Purple Teaming Operator Log
Using Purple Teaming techniques of advanced adversarial and defensive methods, we ensure CSOC performance is optimal.
By combining red and blue teaming scenarios and tracking various tactics and techniques we continuous iterate our methods based on evolving threat landscape and new attack tools.